Reduce attack surface and complexity
By reducing the attack surface, often through resource consolidation, organizations can permanently reduce risk and cost and minimize cybersecurity outages.
Updated on: 2024-07-02
Problem - attack surface too big
The threat landscape is becoming more complex every day. At the same time, the attack surface in many companies is getting bigger and bigger. This combination means security analysts are busier than ever sorting, responding to, and remediating alerts, threats, and incidents across their complex hybrid environments.However, these challenges cannot be solved simply by implementing new security tools. Adding more products in response to new threats not only increases the attack surface, but also often slows down daily operations.
Increasing the number of staff in your Security Operations Center (SOC) is also not the answer as cybersecurity threats continue to grow faster.
The good news is that there are ways to overcome these problems without adding new employees or tools, through:
- Simplify infrastructure or reduce complexity
- Advance infrastructure in the direction of cloud-only
- Outsourcing of some tasks to dedicated experts
Entra ID Conditional Access
The authentication process traditionally worked: a user gives username and password and can access resources in local network.Nowdays, in addition, Entra ID Conditional Access is used to enforce MFA authentication. According to Microsoft MFA can block over 99.9 percent of account compromise attacks.
══
══
Conditional Access uses multiple signals in real time about user identity, device compliance, location and session risk factors, etc. to allow, block or restrict access to company resources.
Since compromised accounts are among the most important attack vectors, blocking access to credentials, even if a correct password is provided, can be invaluable in preventing intrusions.
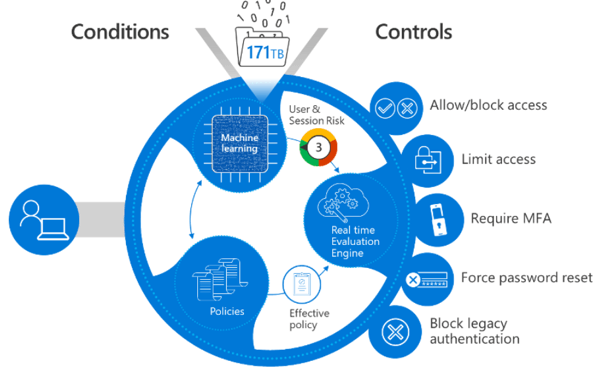
Source: learn.microsoft.com

Increase security and reduce costs
Ready for Cloud Only?
Many organizations have been running a hybrid environment with AD and Entra ID Connect Server for years and replicate user accounts and groups to Entra ID.Several dependencies need to be removed before switching to Entra ID (cloud only), including:
- Switch Windows Clients to Entra ID-Joined
- Migrate Exchange Server to Exchange-Online, incl. MX-Record
- For additional Lagacy servers, use Entra ID DS transitionally
- Entra ID Connect (switch to Password Hash Sync if necessary) stop service
- M365 ADSyncScheduler set to False
- Back up the configuration of AD and Exchange Server, for rollback plan
If you take this step with our support (despite the lack of Microsoft documentation) you will have at once freed up physical and human resources to focus on cloud security.
The future of cybersecurity is cloud-only. It's faster, more responsive to current threats, easier for policy enforcement, control, troubleshooting, updates, and just about everything else in today's world of hybrid work.
Zero Trust Strategy
In the past, local networks were often the only line of defense in the fight against malware, hackers and cyber criminals. Anything outside the local domain was considered a potential threat and defended against with firewalls and similar security measures.Devices on the local network, on the other hand, were considered part of this closed ecosystem and therefore generally considered secure and trusted.
To protect against the increasingly frequent and sophisticated cyberattacks, even users and devices within your own network can no longer be trusted implicitly, but their identities must be constantly verified.
This approach, commonly known as the zero trust model, teaches us: never trust, always verify.
Instead of believing that everything behind the corporate firewall is secure, the zero-trust model assumes breach and verifies each request.
The Microsoft approach to zero trust includes Conditional Access as the main policy engine that includes both policy definition and enforcement.
Reduce complexity
To successfully reduce the attack surface, a complete inventory of all accounts, resources and systems must be documented, because you can not protect what you do not know!This inventory provides information about outdated operating systems, older applications, and who has access to these systems and what access rights they have.
To reduce complexity within the IT environment, the following should be considered:
- Take down obsolete software systems
- Reduce the number of tools and solutions in use
- Segment network with strict access controls
- Train employees on safety best practices, thus preventing security incidents
- Work with a limited number of trusted suppliers and partners
- Define the most important security needs and risks
- Use cloud-based security solutions that offer scalability and easy management
- Keep all software and systems up to date
Proactive security strategy
IT teams struggle to address cyber threats as they evolve, especially when they are already busy with day-to-day tasks, such as resetting passwords and applying patches.Automating as many routine tasks as possible allows IT teams to focus on such tasks, e.g. monitoring the threat landscape, improving cyber risk management and reducing the time to detect and respond to incidents.
Threat hunting is a proactive approach to cybersecurity improvement that finds threats before they can cause harm. This method is based on manual activities and supported by automated techniques.
With Microsoft 365 Defender Advanced Hunting security teams can search for suspicious activity, attack patterns, or unusual behavior to identify threats early and respond appropriately.
We will gladly exchange ideas on how we can support you in establishing or improving a proactive security strategy.
Contact and Support
☏ +49 721 66980 610
Write to us,
you can expect an answer on the same or next working day.
you can expect an answer on the same or next working day.
Get together and talk
We would be happy if you pick a time (right here) and arrange a free online meeting with us via Microsoft Teams. For example, we could talk about whether you can optimise your M365 licenses and reduce costs.
Customer support
We are here to help you with any questions you may have about Microsoft 365 and Azure. You can count on our support at fair prices in the range of 70-90 EUR per hour. We can use your ticket system or our support Jira ServiceDesk, see sample ticket.
You will be supported by security experts who continuously update their Microsoft skills and prove them with manufacturer certificates. This is a MUST for us to keep customer support at the highest level and up to date with the latest technology.
 Copyright 2003 - 2025 Sylbek Cloud Support
Copyright 2003 - 2025 Sylbek Cloud SupportYour IP 216.73.216.89, your resolution , our time



